Shellshock shocked many of the security professionals. Whoa! Wait a minute. Where does it come from?? Okay. Let’s take a deep dive. Shellshock is a security bug in the Bash shell. Which is said to be the most vulnerable bug than the last bug Heartbleed. Stéphane Chazelas discovered the bug on 12 September 2014. The bug was assigned the CVE identifier CVE-2014-6271. This could allow an attacker to gain control over a targeted computer is exploited successfully.
Shell:
It is a command line interpreter between user and kernel. It is more likely a user interface which takes all user inputs (commands) and pass it to the operating system’s kernel and display back its result to the user.
Bash Shell:
Bash is a Unix Shell has written by Brian Fox as a free software. It is initially released in 1989. Since then it has been shipped as the default shell on Linux flavored operating systems and Mac OS X.
Take a look at the Stat & difference between Hearbleed & Shellshock Bash Bug.
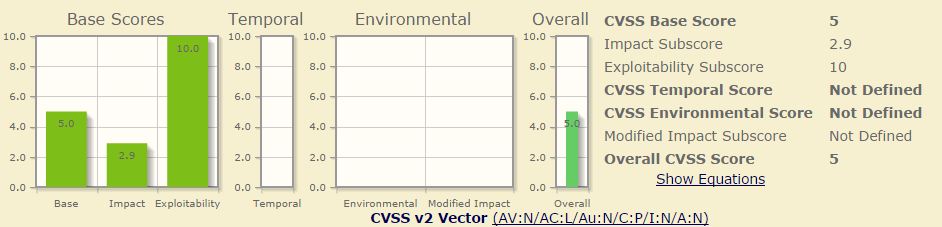
Heartbleed:
* Every operating system running https protocol got affected.
* Attackers can download vital information from the server.
* Attackers need to bypass few other server security settings to access data.
* Not much vulnerable to other non-web related contents in server
* Moderate effect
* NVD Score: 5
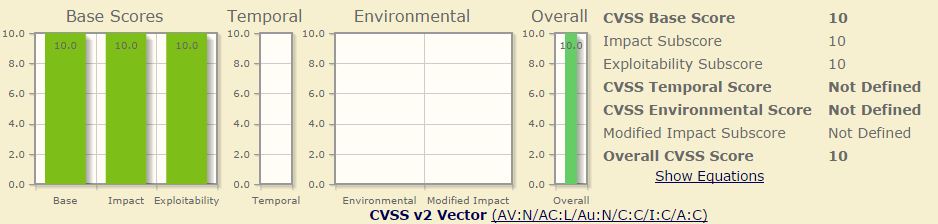
Bash bug:
* Only Linux based operating system which using bash as its shell is affected.
* Attackers can download vital information, can edit settings and delete server files
* No complex security needed to bypass. Any user with simple system knowledge [Along with Google :)] can success!
* If attacker gain access, the whole server is vulnerable
* Extremely dangerous and simple to access.
* NVD Score: 10
For a successful attack to occur, an attacker needs to force an application to send a malicious environment variable to Bash. Stampede situation for security professionals. Panic, being scared, an inability to reason, sleep, walk or talk. This is what you are going to experience when you didn’t fix this bug on your server.
“The realization of the scale and impact of [it] and what I had in my hands was quite scary.” Stéphane Chazelas said.
Thus far, we haven’t been able to find any vulnerabilities agent side, even with an old bash installation, but we strongly recommend updating bash everywhere as soon as possible. If you’re a system admin, you should do this!
Diagnostic Steps:
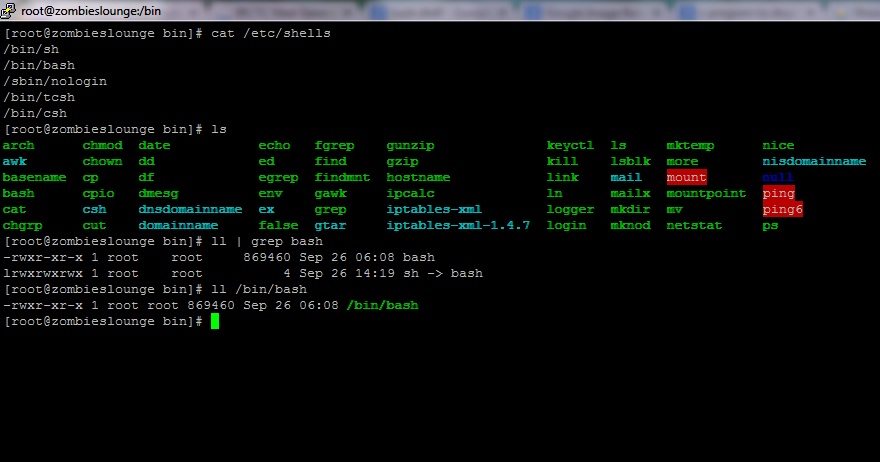
To test if your version of Bash is vulnerable to this issue, run the following command:
$ env x='() { :;}; echo vulnerable’ bash -c “echo this is a test”
If the output of the above command looks as follows: Vulnerable
This is a test
You are using a vulnerable version of Bash. The patch used to fix this issue ensures that no code is allowed after the end of a Bash function.
Thus, if you run the above example with the patched version of Bash, you should get an output similar to:
$ env x='() { :;}; echo vulnerable’ bash -c “echo this is a test”
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for `x’
This is a test
Note: Its a partial fix and REDHAT will update the 2nd stage fix.
Some Basic Security Update links are given below
• Debian—https://www.debian.org/security/2014/dsa-3032
• Ubuntu—http://www.ubuntu.com/usn/usn-2362-1/
• Red Hat—https://access.redhat.com/articles/1200223*
• CentOS—http://centosnow.blogspot.com/2014/09/critical-bash-updates-for-centos-5.html
• Novell/SUSE— http://support.novell.com/security/cve/CVE-2014-6271.html
Caution: Windows does not ship with bash by default, But usually many would have installed bash via cygwin or other means. We at Zombies lounge advice to update these packages applies to Windows as well.
Copyright © 2025 Zombies Lounge. Made With ❤ By Criar Solutions



You must be logged in to post a comment Login